Recently a US non-profit known as the Center of Advanced Defense (C4ADS) released a report titled "Exposing GPS Spoofing in Russia and Syria". In the report C4ADS detail how GPS and Global Navigation Satellite Systems (GNSS) spoofing is used extensively by Russia for VIP protection, strategic facility protection and for airspace denial in combat zones such as Syria. Using simple analysis methods that civilians can use, they were able to detect multiple spoofing events.
GNSS spoofing involves creating a much stronger fake GNSS signal that receivers lock on to, instead of the actual positioning satellites. The fake signal is used to either jam GNSS signals, or report an incorrect location of the spoofers choice.
In the report, C4ADS mention how they used AIS data to identify 9,883 instances of GNSS spoofing which affected 1,311 commercial vessels since the beginning of February 2016. AIS is a marine vessel tracking system similar to the ADS-B tracking system that is used on aircraft. It works by broadcasting on board GPS data to nearby ships for collision avoidance. Although they don't appear to mention their AIS data sources, sites like marinetraffic.com collect and aggregate AIS data submitted by volunteer stations. By looking for anomalies in the collected AIS data, such as ships suddenly appearing at airports, they are able to determine when GNSS spoofing events occurred.
An airport is chosen by Russia as the spoofed location presumably because most commercial drone manufacturers do not allow their drones to fly when their GPS shows them near an airport. This prevents commercial drones from being able to fly in spoofed areas.
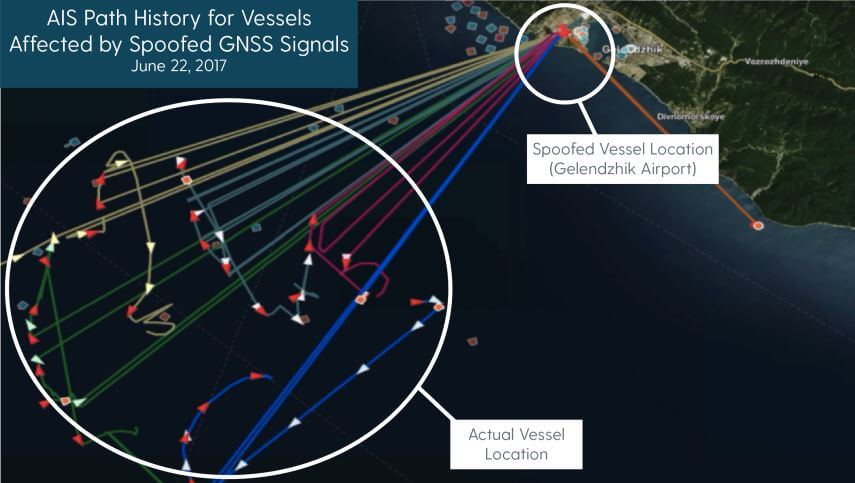
Using AIS data, the researchers were also able to determine that the Russian president uses GNSS spoofing to create a bubble of protection around him. During a visit to the Kerch Bridge in annexed Crimea the researchers found that some vessels near his location suddenly began appearing at a nearby airport. Similar events were detected at multiple other visits by the Russian president.
Another interesting method they used to determine GNSS anomalies was to look at position heatmaps derived from fitness tracking apps. These phone/smart watch apps are often used by runners to log a route and to keep track of distance ran, speeds etc. The researchers found that runners going through central Moscow would sometimes suddenly appear to be at one of two Moscow airports.
In a previous post we showed how Amungo Navigation's NUT4NT+ system was used to detect and locate GPS anomalies at the Kremlin. The C4ADS report also notes how several other Russian government facilities also show signs of GPS anomalies. Of interest, from photos they also saw that the Kremlin has an 11-element direction finding array which could be used to locate civilian drone controllers.
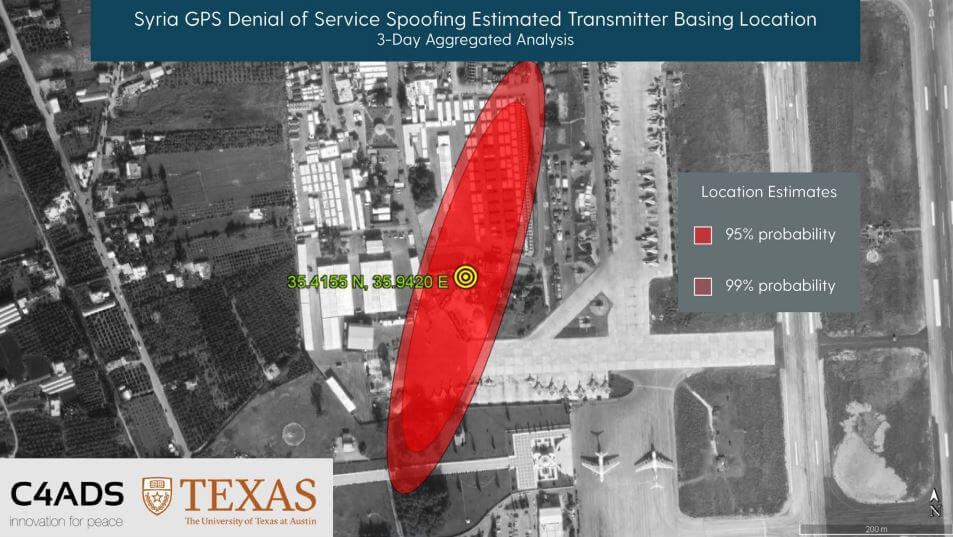
Finally, in the last sections they show how C4ADS and UT Austin used a GPS receiver on board the International Space Station (ISS) to monitor a GPS spoofer at an airbase in Syria. Using Doppler analysis they were able to determine the location of the spoofer and confirm that it is likely the cause of multiple complaints of GPS interference by marine vessels in the area.
The BBC also ran a story on this which is available here.